checksec 2025
checksec / security features of compiled binaries
We recently (November 2021) had a look at the default security features that can be enabled when compiling a binary. More concrete we just ran
|
|
without any additional parameters and then used pwntool’s checksec to check the presence of RELRO, Stack Canaries, NX and PIE support. Those were the results across some popular Linux distributions and versions:
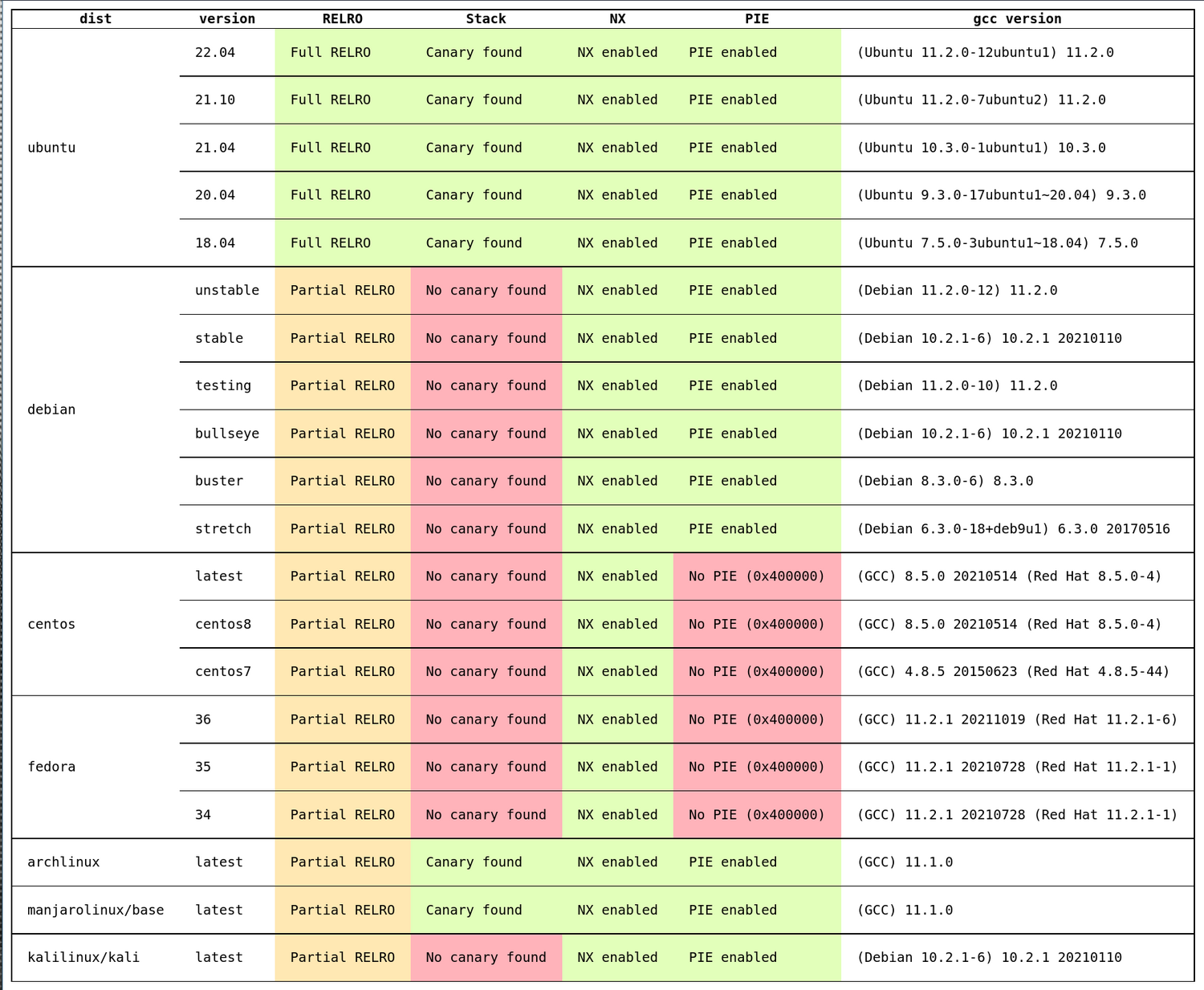
The results show that Debian and Fedora/CentOS don’t use stack canaries by default and Fedora/CentOS doesn’t compile the binary as a Position Independent Executable (PIE) by default. With Kali Linux there are also no stack canaries by default. Full RELRO is only enabled by Ubuntu by default. Also, Ubuntu enables all of the checked features by default.
Note: This does not mean that the distributions’s binaries (e.g., ls, cat, …) are compiled without the security flags as can be seen on this Fedora 35 machine:
|
|
It’s always good to know which features are available and how they can be activated when compiling a program. More information can be found here: https://developers.redhat.com/blog/2018/03/21/compiler-and-linker-flags-gcc
If you want to investigate your favorite Linux distribution use this checksec version: https://github.com/slimm609/checksec.sh and, for example, run:
|
|
to check all binaries in /bin or
|
|
to iterate over all running processes.